Pop-Ups? Just Say “No” — and Close Those Tabs
Making the internet work for YOU means, among other things, getting control of who can follow you aroundDo you get pop-ups in your browser all the time saying, “Let us tell you about new content…” These are push notifications. They offer news and ads (or price changes, etc.) as soon as they are available on the site.
No matter how convenient they sound, just say “no” to push notifications.
Why? Because of what you are really getting into.
A web page, as you see it on your screen, is just a file. It is like a word processing document, an image, or any other file that is transferred from a server to your computer so that your browser can display it for you.
The internet is really a system for transferring files from one reader to another. Even email is a sort of “file,” transferred from host to host. When you click on a link, you connect to a server. It “serves” you the file representing the web page you are trying to reach.
But web pages are often not static; rather, they are dynamically generated. This dynamic generation can require a lot of computing (and hence energy) resources. It can require many round trips between your computer and the server. To reduce the time and server resources required, servers are allowed1 to push processing to the host—that is, to your computer, tablet, or phone.
A server can push two kinds of processes to your computer. The first is a web worker, which enables some part of a web page to be displayed on your computer. Think of a mortgage calculator, for instance: The server provides the formulas and parameters but, based on the data you enter, the calculations are performed on your computer.
The second kind — the one we are interested in here — is called a service worker. It opens a semi-permanent channel between your local web browser and the server, which allows the server to push notifications to your local system. This process creates local notifications like “Founder’s Day Sale!” or “Furies Win 7-6 on Overtime Goal!” The placement of the service worker is shown in the illustration below:
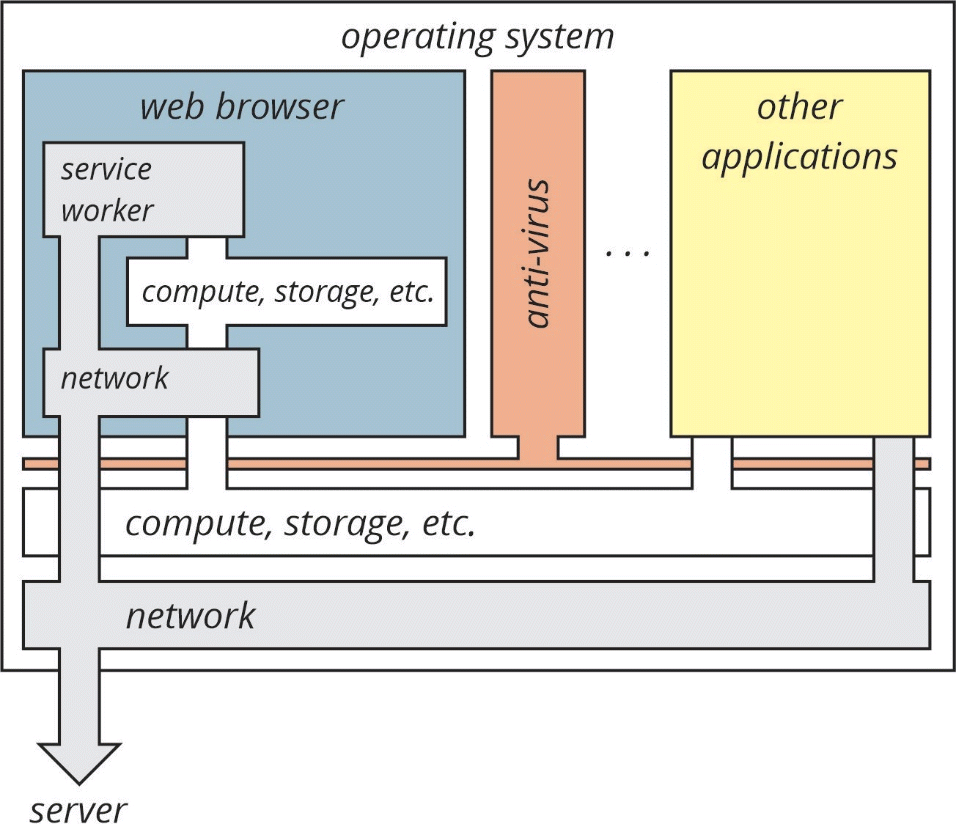
The service worker that makes these push notifications possible is inside your web browser.2 But it also has direct access to the network in order to reach the server. Further, these service worker processes are persistent—they are run automatically by the web browser every time you launch it.
In other words, once you allow notifications from a retail site, the site creates a service worker on your computer. The next time you start your web browser, this service will start even if you do not visit the retail site’s web page.
And that’s not all. These service workers also have access to any tabs you have opened in your browser. In fact, most web sites you open have access to the other tabs you have opened in your browser.
So by accepting push notifications, you are allowing a server to open a direct “conduit” through the public internet to your computer. You are allowing that server to allocate processing and memory resources on your computer, and also allowing that server to “see” (to some degree) what other tabs you have open in your browser and at least some of the information available on those tabs.
If allowing these notifications sounds like a perfect avenue for an attacker, that’s because it is. This attack surface is a very large hole in the security of your computer.
What about anti-virus software? Anti-virus software should catch any kind of “evil activity” running on your computer, right? Not in this case. Because these service workers run within the web browser, your anti-virus software cannot “see” what they are doing.
The bottom line: Do not accept push notifications from sites, even sites you trust. The tradeoff between being a more proactive seeker on the web and a more passive consumer of whatever a site might want to push at you is just not worth it. There are other ways to keep up with the “news,” such as it is, and you can always reload a page to find out about up-to-the moment sales or new products. You can also sign up for email lists and RSS feeds to keep up with current information.
As an aside, you should always close tabs you are not actively using. If you want to save them for some future time (even a few minutes from now), you can save them into a speed dial or bookmark. The efficient use of bookmarks and other techniques to get back to information quickly can reduce the possibilities for cross-tab attacks, and even reduce the amount of processing and memory (and hence power) your computer uses.
Internet security, like home security, requires intelligent awareness and active participation.
Notes:
1 They are allowed to do so by the HTML (Hypertext Markup Language) specifications. HTML is the format for describing and rendering a web page. As the name implies, it uses markups to describe how the page should look on your screen if you click on a URL (Uniform Resource Locator) or enter it into your web browser.
2 Technically, the service worker runs within the context of the web browser, using processor and memory resources allocated to the browser.
More from Russ White on making the internet work for you:
Should You Pay For a Virtual Private Network (VPN)? Here’s what a VPN can and can’t do for you. In some cases, specifically when you are using public wireless services, using a VPN can add measurably to your privacy and security. But VPNs are not a “silver bullet” in solving the many security and privacy issues users face today.
The internet’s structure builds in privacy flaws. The Domain Name resolver knows every service you visit, and every service those services rely on, as you move around the internet
You think you have nothing to hide? Then why are Big Tech moguls making billions from what you and others tell them?
and
Why you can’t just ask social media to forget you. While we now have a clear picture of the challenges current social media pose to people and cultures, what to do is unclear.
